Imagine
your business as a bustling office building. Every day, employees, clients, and
partners come and go, accessing sensitive data and resources. Traditional
security approaches are like trying to secure this building with a single,
easily bypassed front door and a few security guards patrolling the main lobby.
This
might have worked in the past, but in today's world of sophisticated cyber
threats, it's simply not enough. Hackers can exploit vulnerabilities, trick
employees, or even gain access through seemingly harmless devices like printers
or smart coffee machines. Once inside, they can wreak havoc, stealing data,
disrupting operations, and damaging your reputation.
What is Zero Trust Security?
Zero
trust, in simple terms, means never trusting anyone implicitly. Every user and
device, both inside and outside your network, is constantly verified before
gaining access to any resources. Think of it like a high-security building
where everyone needs to show their ID and get scanned before entering,
regardless of their relationship to the company.
The
Key Principles of Zero Trust:
- Least privilege
access: Users only get access to the specific resources they
need for their job, minimizing the potential damage from any breach.
- Continuous
monitoring: All activity within the network is constantly
monitored for suspicious behavior.
- Micro-segmentation: The network is divided into smaller, isolated segments to limit the spread of any attack.
- Multi-factor authentication: Strong authentication methods like two-factor authentication are used to verify user identity.
Zero Trust vs. Traditional Security: A Tale of Two Worlds
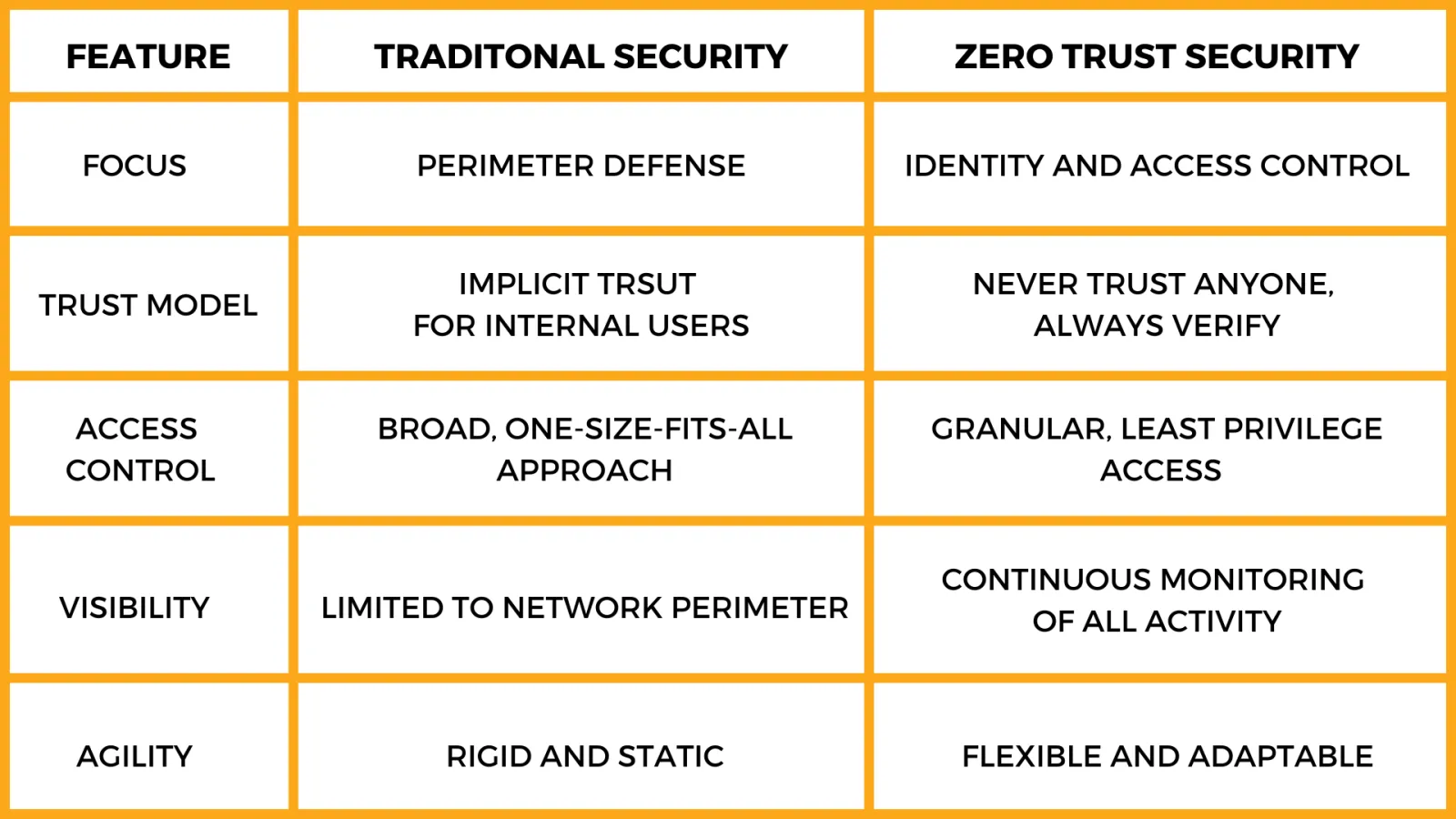
Why
Businesses Need Zero Trust Security:
In
today's cloud-powered and remote-work world, the traditional "castle and
moat" approach is simply outdated. Here's why zero trust is essential for
your business:
- It protects against
insider threats: Malicious actors or compromised accounts can cause
significant damage in a traditional network. Zero trust minimizes this
risk by limiting access and monitoring all activity.
- It secures remote
work: With employees working from anywhere, traditional
perimeter defenses are ineffective. Zero trust ensures secure access
regardless of location or device.
- It complies with
regulations: Many data privacy regulations require strong access
controls. Zero trust helps businesses meet these compliance requirements.
- It protects your data: By minimizing access and encrypting data, zero trust makes it harder for attackers to steal sensitive information.
Building Your Zero Trust Bridge:
Implementing
zero trust is not a one-size-fits-all process. However, here are some steps you
can take:
- Conduct a security
assessment: Identify your vulnerabilities and critical assets.
- Develop a zero trust
strategy: Define your goals and choose the right technologies.
- Implement identity
and access management (IAM) solutions: Control who has
access to what.
- Enable multi-factor
authentication (MFA): Add an extra layer of security to user logins.
- Segment your network: Divide your network
into smaller, isolated zones.
- Monitor and analyze
activity: Look for suspicious behavior and respond quickly.
VECTOR CHOICE ADVANTAGE
Implementing zero trust can be complex, but you don't have to go it alone. We can help you assess your needs, develop a strategy, and implement the necessary technologies.Zero trust is not just a buzzword; it's a fundamental shift in how we think about cybersecurity. By building a secure bridge instead of a moat, you can protect your business from today's evolving threats and create a more secure future.
Remember, your business is only as secure as its weakest link. Don't wait for a
breach to happen. Build your zero trust bridge today and make sure your data is
always protected. Schedule a 10-minute discovery call today to learn more!


