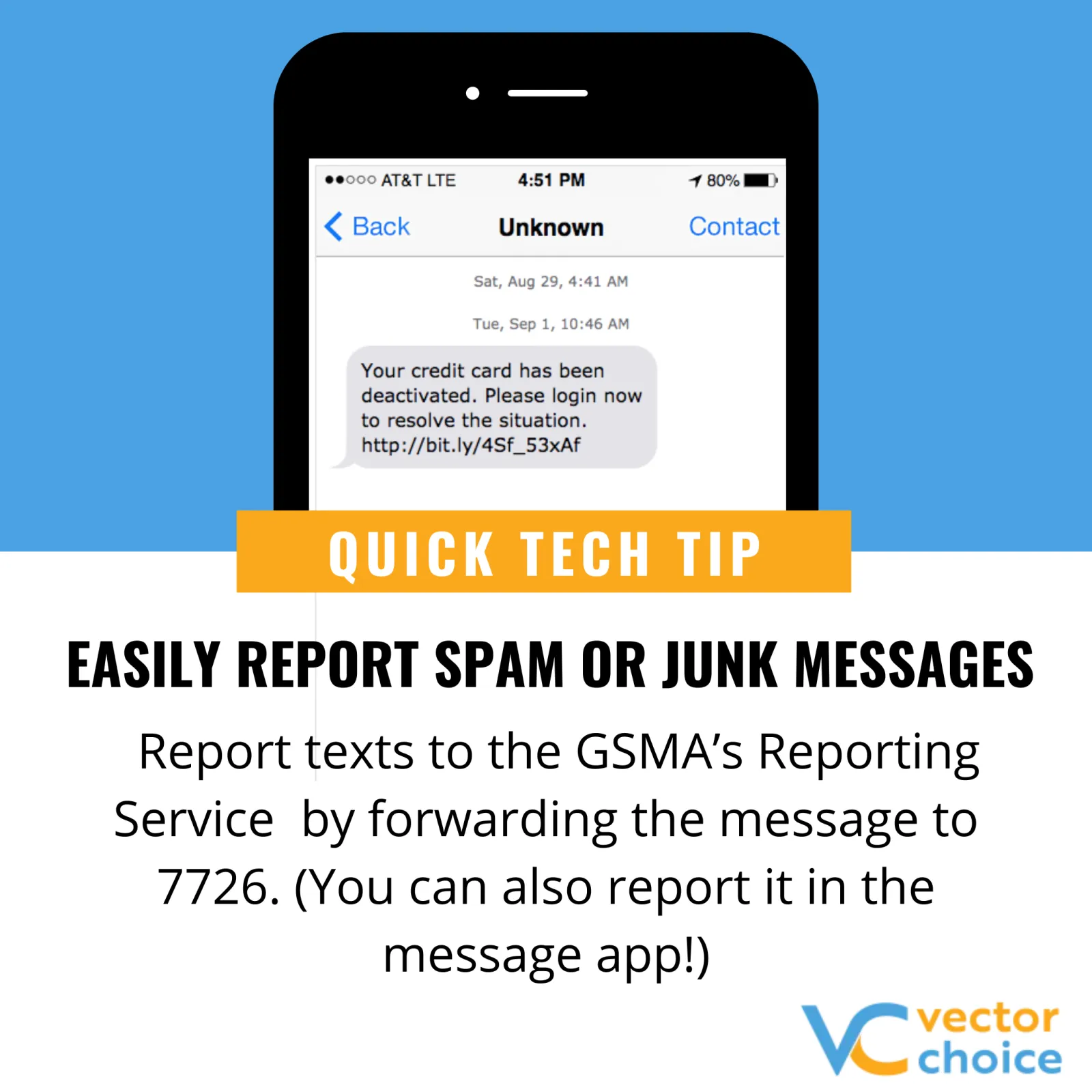
Cyberattacks are a growing concern for businesses of all sizes and across all industries. While prevention is crucial, being prepared for the possibility of an attack is equally important. Here's why having a well-defined incident response plan (IRP) is essential and what steps you should take if your business experiences a cyberattack.
Why is an IRP crucial?
- Minimize Damage: A
well-rehearsed IRP helps you respond swiftly and effectively to a
cyberattack, potentially limiting the extent of damage and the duration of
disruption to your business operations.
- Contain the Threat: A structured
plan outlines clear steps to isolate the affected systems and contain the
threat, preventing further escalation and minimizing the potential for
data loss or compromise.
- Facilitate Recovery: The IRP guides
your team through the critical steps necessary for recovery, including
data restoration, system repair, and restoring normal business operations.
- Maintain Compliance: Certain
industries have regulations mandating specific actions in response to
cyberattacks. An IRP ensures your organization meets these compliance
requirements.
What to do when a cyberattack happens
1.
Contain the Threat:
- Identify and isolate: Immediately
identify the affected systems and isolate them from the network to prevent
further spread of the attack.
- Disable remote
access: Disable remote access points to compromised systems to prevent
attackers from gaining further control.
- Shut down affected
systems: If necessary, shut down critical systems to prevent further damage
and data loss.
2.
Assess the Situation:
- Gather information: Assess the
scope of the attack, including the affected systems, data potentially
compromised, and the potential impact on your business.
- Preserve evidence: Secure and
preserve any potential evidence, such as logs, network traffic, and
infected files, for forensic analysis and investigation.
3.
Respond and Recover:
- Activate your IRP: Follow the
established steps outlined in your IRP, involving relevant personnel and
initiating necessary actions such as notifying law enforcement and
regulatory authorities.
- Commence remediation: Begin
remediation efforts to remove the attacker from your systems, address
vulnerabilities, and restore affected systems to functionality.
- Data recovery: Implement your
data recovery plan to restore lost or compromised data and ensure business
continuity.
4.
Learn and Improve:
- Conduct a
post-incident review: Analyze the incident to understand its cause,
identify vulnerabilities exploited, and evaluate the effectiveness of your
response.
- Update your IRP: Based on the
learnings from the incident, update your IRP to address any identified
weaknesses and improve your preparedness for future threats.
Partner with Vector Choice
Vector Choice offers valuable
expertise and resources in developing and implementing robust IRPs. We can
assist you in:
- Creating a customized
IRP: Develop a plan specific to your business needs and industry
regulations.
- Conducting security
assessments: Identify potential vulnerabilities and weaknesses in your systems.
- Providing incident
response training: Train your employees on their roles and
responsibilities during a cyberattack.
- Offering ongoing
security monitoring: Proactively monitor your network and systems for
potential threats.
By having a well-defined
incident response plan and potentially partnering with Vector Choice, you can
significantly increase your organization's preparedness and ability to respond
effectively to a cyberattack, ultimately minimizing damage and ensuring a
quicker recovery.
Schedule a 10-minute discovery call today to learn more about how we can help
protect your business!